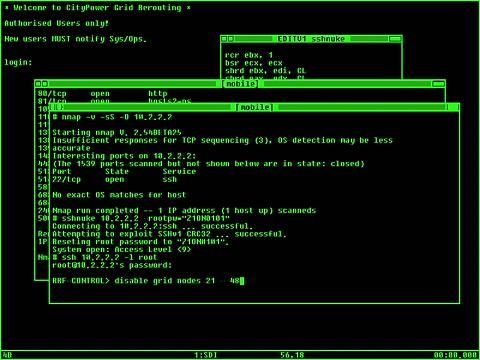
The usage of computers in movies has always been quite hit and miss. The Matrix Reloaded movie had realistic depictions of the usage of the NMAP port scanning command and the use of the ssh command to login remotely to the target machine and execute commands to shutdown the power plants to buy the keymaster enough time so that Neo could visit the Architect. The ssh port scanner command is very useful for analysing a local or remote machine for open ports that could be a security hole. The nmap security scanner is a very popular tool to check machines; but it is used by malicious people as well. The point though is that once you have secured your machine and you have implemented a proper security procedure to deal with unwarranted intrusions, the threat posed by the many Internet threats that are growing day-to-day should not be the danger that the media dramatizations make it out to be. The Matrix movie was quite an amazing cinematic experience when it was first released; the idea of a virtual reality world inhabited by the collective consciousness of humanity that are unaware that the entire world is just a simulation is something that could be a reality; but the unbearable fact is that the humans could be nothing but a brain in a jar and they would have no body and nothing to escape the Matrix in.
using the nmap commands used in the Matrix movie in real life results in a useful output. This command is used against the facebook.com website and it seems to be running on the super secure OpenBSD UNIX operating system. The sshnuke command Trinity used to break into the UNIX servers in the movie was a program she wrote herself using a known exploit present in the ssh package at that time. Some movies show ridiculous things on computers; the Tron Legacy movie with the ENCOM UNIX operating system that the company developed was another movie that got the use of computers right. The ps -ef and kill -9 commands are correct; the computer user is trying to stop a malicious program that is running on a UNIX computer using a cool touch keyboard. This keyboard has been built using what looks like two iPads; quite an expensive keyboard indeed, unless you work at Apple. But it is a similar concept, but I prefer a proper keyboard. The technology used to create the Tron Legacy touch keyboard is available and worth trying if you have the hardware. Now all you need is the leaked ENCOM operating system and you are good to go.
Scanning facebook.com to look for open ports on the web server. This is a good use of nmap.
flynn-grid-runner ~ # nmap -v -sS -O 66.220.149.88 Starting Nmap 5.21 ( http://nmap.org ) at 2012-09-13 20:27 EST Initiating Ping Scan at 20:27 Scanning 66.220.149.88 [4 ports] Completed Ping Scan at 20:27, 0.18s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 20:27 Completed Parallel DNS resolution of 1 host. at 20:27, 0.00s elapsed Initiating SYN Stealth Scan at 20:27 Scanning facebook.com (66.220.149.88) [1000 ports] Discovered open port 80/tcp on 66.220.149.88 Discovered open port 443/tcp on 66.220.149.88 Discovered open port 843/tcp on 66.220.149.88 Completed SYN Stealth Scan at 20:28, 57.56s elapsed (1000 total ports) Initiating OS detection (try #1) against facebook.com (66.220.149.88) Retrying OS detection (try #2) against facebook.com (66.220.149.88) Nmap scan report for facebook.com (66.220.149.88) Host is up (0.23s latency). Not shown: 997 filtered ports PORT STATE SERVICE 80/tcp open http 443/tcp open https 843/tcp open unknown Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING) : OpenBSD 4.X (85%) Aggressive OS guesses: OpenBSD 4.3 (85%) No exact OS matches for host (test conditions non-ideal). Uptime guess: 0.000 days (since Thu Sep 13 20:28:13 2012) TCP Sequence Prediction: Difficulty=261 (Good luck!) IP ID Sequence Generation: All zeros Read data files from: /usr/share/nmap OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 65.01 seconds Raw packets sent: 2096 (95.812KB) | Rcvd: 63 (3420B) flynn-grid-runner ~ # |
The ps -ef command used in Tron Legacy. This is what it does on my machine; looking for all instances of su.
flynn-grid-runner ~ # ps -ef | grep su root 25 2 0 Sep12 ? 00:00:00 [sync_supers] root 3010 1 0 Sep12 ? 00:00:18 /sbin/mount.ntfs /dev/sda1 /media/Elements -o rw,nosuid,nodev,uhelper=udisks,uid=1000,gid=1000,dmask=0077,fmask=0177 root 11005 1 0 19:46 ? 00:00:02 /sbin/mount.ntfs /dev/sdi1 /media/Ubuntu 11.04 i386 -o rw,nosuid,nodev,uhelper=udisks,uid=1000,gid=1000,dmask=0077,fmask=0177 root 11334 10791 0 19:52 pts/0 00:00:00 sudo su - root 11339 11334 0 19:53 pts/0 00:00:00 su - root 11347 11339 0 19:53 pts/0 00:00:00 -su root 12051 11347 0 21:06 pts/0 00:00:00 grep --colour=auto su flynn-grid-runner ~ # |
More reading here: here.