Amazon Web Services is a very powerful way to run a virtualized server in the cloud, but there are some tips that will help you greatly when deploying a server for the first time. SSH access is one.
Changing the SSH port from 22 to 443 in the /etc/ssh/sshd_config file will help access when you are behind a firewall or a proxy. Then amend your Security Group to reflect the new changes.
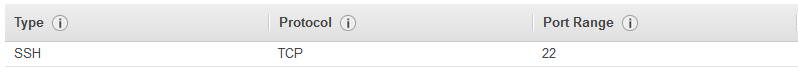
The best SSH client for accessing your AWS instance is the Bitvise SSH client. This can import the SSH keys from your Linux instance directly without having to convert them as you do with Putty. Using an OpenVPN VPN on your Amazon AWS instance is the best way to securely access the instance over SSH. I would use port 443 for the VPN and then use the SSH connection over port 22, but only over a secure Virtual Private Network connection. This is the most secure configuration.
Make regular backups of your configuration. This can easily be restored if there is an issue with the system.
Here is a posting with a nice script to work as a shortcut to create an OpenVPN server, this will really help out.
With your OpenVPN configuration, it is possible to set or change the passphrase for the server.pem file.
https://securitronlinux.com/bejiitaswrath/set-or-change-a-passphrase-for-an-openvpn-server-key/.
How to create a new set of keys for your OpenVPN instance.
Sample client.conf file for OpenPVN. This is how to configure an OpenVPN client to connect to a remote server at 52.63.195.144, with the port set to 443.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 | client ;dev tap dev tun ;dev-node MyTap ;proto tcp proto tcp remote 52.63.195.144 443 resolv-retry infinite nobind user nobody group nogroup persist-key persist-tun http-proxy proxy.det.nsw.edu.au 8080 stdin basic mute-replay-warnings ca ca.crt cert john.crt key john.key ns-cert-type server ;tls-auth ta.key 1 ;cipher x comp-lzo verb 3 ;mute 20 |
This is the OpenVPN configuration file I was using for my VPN on Amazon AWS for testing.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | server 10.8.0.0 255.255.255.0 verb 3 duplicate-cn key server-key.pem ca ca.pem cert server-cert.pem dh dh.pem keepalive 10 120 persist-key persist-tun comp-lzo push "redirect-gateway def1 bypass-dhcp" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" user nobody group nogroup proto udp port 1194 dev tun1194 status openvpn-status-1194.log |
The IP address to connect to the server for SSH would be 10.8.0.0. This is routed through the private VPN connection.
Running a VPN is the best and safest way to access your Amazon AWS Linux shell and administer the machine. These sample files and tips should really help you out.