A recent Mr Robot episode featured a TOR hidden site that was used to traffic kidnapped people. This is depicting the TOR service as a haven for illegal activities, when it is not even that secure in the first place. It is mainstream now, with everyone talking about it and investigating it for themselves. Therefore, it is not the secret club it used to be. Freenet and Marinas web might be even more secure and hard to access versus TOR .onion sites. In the “Mr Robot” pilot episode the main character mentions intercepting traffic from a tor exit node, which he eventually uses to expose an individual who is running a hidden service. There is information about TOR exit nodes here: https://hackertarget.com/tor-exit-node-visualization/. Apparently, it is possible to monitor traffic exiting a exit node if it is unencrypted. This could be abused to compromise a TOR service.
Here is a discussion of how the exit node could have been compromised: https://www.reddit.com/r/MrRobot/comments/3mo71e/in_the_first_episode_how_would_elliot_gained/.
This is the URL of this TOR hidden service. This is not a real working TOR URL of course, but is a realistic URL and could exist.
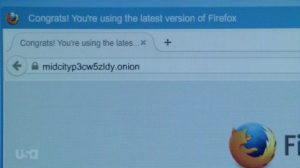
This is just bringing the TOR network out into the open and making people afraid of what could exist on a hidden service. But compromising the server was not that hard apparently…
Quoted from: https://www.reddit.com/r/MrRobot/comments/37n8p3/episode_one_discussion/crsinic.
The local traffic from Ron to his servers (where a hidden service was hosted) is what he sniffed. Remember, Elliot is physically at the location and on the connection that Ron is using to communicate with his servers. Even if Elliot had to compromise or setup an exit node to sniff & decrypt Ron’s further actions, it’s rather implied that all he had to do was root Ron’s servers regardless of Tor usage.
“I started intercepting all the traffic on your network.” “I own everything, all your emails, all your files, all your pics.”
That’s not something you get from just watching his traffic via Tor exit node control. He had to compromise his box to own everything.

So, accessing the physical server and gaining a login was how he managed to take the guy down. That is how he was able to compromise the server, he sniffed the traffic the guy was sending and receiving by using the same WIFI network he was on and capturing network packets to gain login data. If the guy had been using HTTPS and/or a VPN to connect, he might have had more protection from Elliot who was capturing his whole session. But he needed to learn more about network security and this is a good lesson to learn. If he had stayed away from the whole deep web crime thing, then he would be fine, but no. That is why anyone using public WIFI should be very careful. You never know who might be listening on the connection. Kali Linux is shown a great deal in this TV show, this custom Linux distribution is very popular in the penetration testing world. There are so many tools available in this distribution and it is very good at cracking WIFI and listening in on network traffic. With Wireshark you can do such things as listen in on VOIP traffic generated by IP phones and then reconstruct the audio and listen to it. Or gather files transferred over a network connection if someone is browsing the web.
If someone has good skills already and they want to test them out, the DARPA Cyber Grand Challenge would be a good bet. https://www.cybergrandchallenge.com/. This is a computer security cracking challenge that would be a good test of your skills. The Cyber Grand Challenge (CGC) seeks to automate this cyber defense process, fielding the first generation of machines that can discover, prove and fix software flaws in real-time, without any assistance. If successful, the speed of autonomy could someday blunt the structural advantages of cyber offense.