I had captured a handshake when I connected my phone to my WIFI at home using wifite. This allowed me to test out the aircrack suite to crack a WIFI passkey.
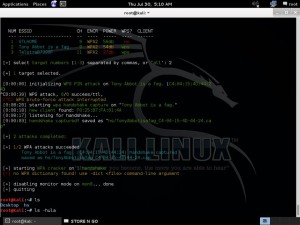
This captured the WPA2 handshake when I reconnected my phone to my wireless network.
I am using aircrack-ng against my .cap file with the rockyou.txt password file. I had to add my passkey to this file as it would not have been included already, as it was far too complex.
jason@darkstar:~/Desktop$ aircrack-ng TonyAbbot_C4-04-15-4D-44-24.cap -w rockyou.txt |
This is the result of this action. I have managed to crack the hash and find the passkey in the wordlist.
Aircrack-ng 1.2 beta3 [00:00:05] 8372 keys tested (1571.21 k/s) KEY FOUND! [ tomcatff12whigFFG ] Master Key : 5A 82 ED F2 4F 6E F1 42 D7 B5 F6 11 F6 F9 6B 58 6F D9 04 A3 ED 6F 8A D0 07 2A E3 4E 93 8A 66 6A Transient Key : 56 8F 34 6E 43 F7 59 C4 35 B0 58 1F 48 29 1C 6F EC 47 BE A4 8D 6B 46 CE F6 59 ED B8 E6 3F 4B 0E C0 6F 41 A7 5A 88 02 B8 13 48 0C 37 4A 60 BD 1E 3F 69 73 9B E2 D1 DA 24 B6 72 C5 8E 9E 11 FA B8 EAPOL HMAC : EB 8C BB B2 FC 45 4C DC 75 57 BD 2A 6E 4F F1 70 jason@darkstar:~/Desktop$ |
This is how easy it can be to attack a wireless network. The key is to wait patiently for someone to connect to the network, or to de-authenticate them and wait for them to reconnect to capture a WPA2 handshake containing the WPA2 PSK. Having an even bigger wordlist would be a better option, the bigger it is the better as it is more likely that their password will be in it. That is the main concern.
Newer posting with full steps included cracking a WIFI network with aircrack.